from Reuters: Technology News https://ift.tt/2OkKJa6
Uber begins accepting cash in Mexico City, tapping key market
from Reuters: Technology News https://ift.tt/2OkKJa6
Apple held talks to take stake in iHeartMedia: FT
from Reuters: Technology News https://ift.tt/2PBPjpa
Father of Web says tech giants may have to be split up
from Reuters: Technology News https://ift.tt/2zi33uZ
Testy talks, tangled taxes: Amazon's slow push into Brazil's retail jungle
from Reuters: Technology News https://ift.tt/2Q8YTwT
Hong Kong securities regulator to propose 'sandbox' for crypto exchanges
from Reuters: Technology News https://ift.tt/2Q8JjkT
Apache Releases Security Update for Apache Tomcat JK Connectors
The Apache Software Foundation has released a security update to address a vulnerability affecting Apache Tomcat JK Connectors 1.2.0 to 1.2.44. A remote attacker could exploit this vulnerability to obtain access to sensitive information.
NCCIC encourages users and administrators to review the Apache security advisory for CVE-2018-11759 and apply the necessary update or mitigation.
This product is provided subject to this Notification and this Privacy & Use policy.
from US-CERT: The United States Computer Emergency Readiness Team https://ift.tt/2ADUTiI
VW and Ford in talks on self-driving and electric vehicles: source
from Reuters: Technology News https://ift.tt/2qlwEzH
U.S. Supreme Court divided over Google privacy settlement
from Reuters: Technology News https://ift.tt/2PwzQqj
Check Point CloudGuard and VMware Deliver Advanced Security at Scale and Speed at VMworld Europe 2018
By Amir Kaushansky, Sr. Product Manager, Cloud Security
In August this year, I had the pleasure of attending and presenting at my first VMworld, Las Vegas, and I’m glad to say it will not be the last. However, in this case, what happens in Vegas will certainly not stay in Vegas. We are excited to be in Barcelona, Nov. 5-8 as a platinum sponsorship next week. We invite you to attend our sessions on Nov. 6 and Nov. 7. Let’s take a deep dive into what we will present with VMware to deliver agile and elastic cloud infrastructure.
The session was co-presented with Jeremiah Cornelius, VMware’s Partner Architect for Check Point, on “A Practical Guide for Delivering Advanced Security at Scale & Speed in SDDC”, with the following main takeaways:
- NSX provides a secure platform to deliver VMs.
- Check Point CloudGuard IaaS provides advanced security on top of NSX with features such as IPS, Application Control, IPsec VPN, Antivirus, AntiBot and award-winning SandBlast sandboxing technology.
- Check Point and VMware has a very strong partnership. Check Point is a design partner to features in NSX such as the multi-channel and Check Point is integrated with many VMware products such as vRealize, vRNI and more.
I was able to showcase that the NSX – CloudGuard integration provides extra value via a demonstration using Ransomware, we installed a Windows environment with NSX firewall rules allowing port 445 only. The ransomware was merely installed on one machine but spread spread across the entire cluster. Not exactly the kind of incident you want happening across your systems, right?
However, we then used the same test, but this time we had CloudGuard IaaS installed and were able to prevent the entire attack.
While this is obviously the desire outcome, my main area of interest concerned the NSX-T Data Center as I had heard it is no longer just a private cloud deployment but can also act as the network virtualization and security platform that enables the virtual cloud network, a software-defined approach to networking that extends across data centers, clouds, endpoints, and more. The idea with NSX-T Data Center that is most interesting is that networking and security are brought closer to the application wherever it is running, from VMs to containers, bare metal and multiple hypervisors.
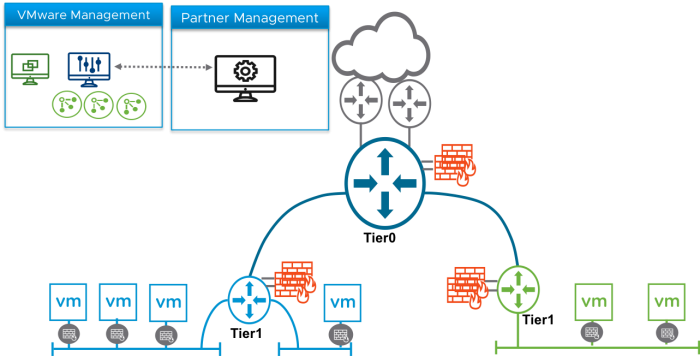
Figure 1: NSX-T Edge Routers Deployment
With my VMware counterparts, we discussed the various integration points:
- Insertion:
- North-South – from/to the internet or external network to the NSX-T T Data Center workloads.
- East West – between workloads on the NSX-T Data Center.
- Inventory – CloudGuard reads the inventory from NSX and allows the security operator to use objects from the inventory as part of the security policy. CloudGuard watches these objects and updates the gateway on any change that might occur on the NSX side.
We formalized an action plan and kicked off the first two items: North-South insertion of CloudGuard IaaS and NSX-T inventory.
As a result, I’m happy to announce that Check Point has certified and released this new integration and we now support the insertion of CloudGuard IaaS to T0 and T1 edge routers in a three-step, easy-to-use wizard.
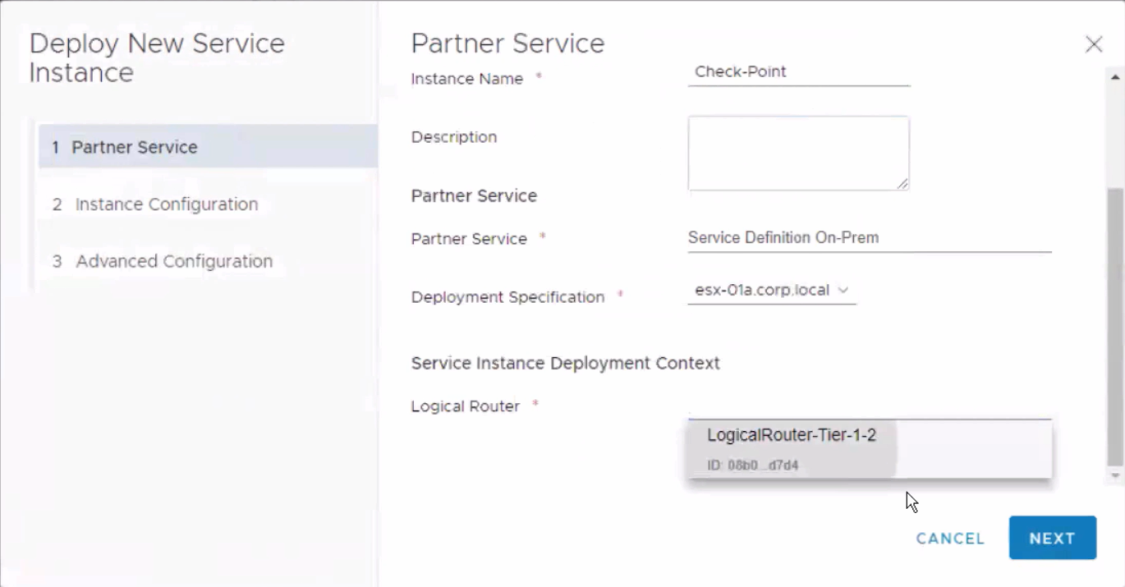
Figure 2: North-South insertion Wizard in NSX-T Data Center
By doing so, Check Point CloudGuard IaaS will boost its ability to deliver advanced threat prevention security to VMware NSX-T Data Center environments. Designed for the dynamic requirements of cloud-based data centers, CloudGuard is a prime solution for providing automated security provisioning coupled with the comprehensive protections. Centrally managed across hybrid infrastructures, CloudGuard provides consistent security policy enforcement, full threat visibility across physical data centers, SDDCs, and public cloud environments.
As mentioned earlier, what happened in Vegas did not stay in Vegas and the same goes for VMware Europe in Barcelona on November 5-9. Attend the session in-person and ask questions. We look forward to you dropping by the Check Point booth, P413, and checking out for yourself the integrated VMware-CloudGuard solution story.
Join our breakout sessions and hands-on labs:
- You can still get burned when it’s cloudy, presenter Yariv Fishman Head of Product Management, Cloud Security and IoT [NET1020BES]– Tue., 06 November, 12:30 – 13:30
- Practical Guide for Delivering Advanced Security at Scale and Speed in SDDC, [HYP1022BES] presenters Jeremiah Cornelius Partner Alliances Architect and Javier Hijas, Cloud Security Leader for Check Point on Wed., 07 November, 14:00 – 15:00
- Check Point CloudGuard and VMware NSX – Advanced SDDC Security, [SPL-1924-01-NET_E] Hau Tran, Senior Solutions Engineer, VMware and Glenn Gauvin, Cloud Technical Marketing Engineer Check Point

The post Check Point CloudGuard and VMware Deliver Advanced Security at Scale and Speed at VMworld Europe 2018 appeared first on Check Point Software Blog.
from Check Point Software Blog https://ift.tt/2qiC6mY
Information security: How Hackers Leverage Stolen Data for Profit

Data theft is inarguably big business for hackers. This has been proven time and time again when big-name companies and their customers are involved in a data breach. As these instances appear to take place more often, and the number of stolen or compromised files continues to rise, it’s worth looking into exactly what hackers do with this information after they’ve put so much effort into stealing it.
While some data breaches involve low-hanging fruit – including default passwords and other sub-standard data protection measures – other attacks include increasingly sophisticated cybercriminal activity, backed by in-depth social engineering and research into potential targets. Thanks to these efforts, more than 2.6 billion records were stolen or compromised in 2017, a staggering 88 percent rise from the amount of data hackers made off with in 2016, according to Information Age.
But what takes place after a successful breach and data exfiltration? With all of this information in hand, where do hackers turn next to generate a profit?
Type of data dictates price, post-theft malicious activity
As Trend Micro research shows, the process that stolen data goes through after the initial breach depends largely upon the type of data and from what industry it was stolen.
Personally identifiable information (PII) can include a whole host of different elements and is stored by many brands to support customer accounts and personalization. Researchers discovered that once hackers bring this information to underground markets, it can be used to support identity fraud, the creation of counterfeit accounts, illicit money transfers, the launch of spam and phishing attacks, and even blackmail, extortion or hacktivism.
Let’s take a look at the ways in which other types of stolen data can be used once hackers gather it and bring it to underground marketplaces:
|
|
One theft leads to another
A main motivation of hackers is to make off with as much stolen information as possible. This thought process is applied not only to data breaches of specific companies, but also of the data belonging to individual users as well.
“More than 2.6 billion records were stolen or compromised in 2017.”
Take stolen account credentials, for example. A hacker will often leverage a stolen username and password to support further malicious activity and data theft in the hopes of compromising even more personal information.
“Theft of user credentials might even be more dangerous than PII, as it essentially exposes the victim’s online accounts to potential malicious use,” Trend Micro researches pointed out. “Email is often used to verify credentials and store information from other accounts, and a compromised email account can lead to further instances of fraud and identity theft.”
In such instances, a hacker can utilize stolen account credentials to fraudulently access an individual’s email. This may provide the cybercriminal with an email that includes a credit card invoice, giving them even more information for theft, and even the potential to steal, use or sell the victim’s credit card details for further fraud.
What’s more, as Trend Micro researchers noted, certain types of data are often interrelated, and the theft of one set of data often means the compromise of another, connected set. With health care files, for instance, a health care provider may store not only a patient’s medical history, but also their payment information as well. In this way, a breach of the provider could result not only in the exposure of medical details, but patient financial information as well.
What is data worth on underground marketplaces?
As Trend Micro’s interactive infographic shows, there are several different underground marketplaces existing all over the world, and the amount of profit hackers are able to generate depends on where they sell stolen information and the type of details their haul includes.
Experian data fro 2018 shows how profits for certain types of data can quickly add up for hackers, including for assets like:
|
|
Hackers also engage in data bundling, where individual pieces of stolen information are linked and packaged together, and then sold in a premium bundle for a higher price. These more complete, fraudulent profiles can include an array of information, including a victim’s name, age, address, birth date, Social Security number, and other similar information.
Working to prevent data theft
As the profit totals hackers can generate from stolen data continues to rise, it’s imperative that businesses and individual users alike take the proper precautions to safeguard their sensitive information.
This includes replacing default security measures with more robust protections, including strong passwords and multi-factor authentication, where applicable. Organizations should also limit access to especially sensitive information and databases to only those authorized users that need to utilize this data.
User education can also be a considerable advantage in better preventing information left. Users that are aware of current threats and know not to click on suspicious links or open emails from unknown senders can represent an additional layer of security against unauthorized access and cybercriminal activity.
To find out more about how to improve data prevention efforts within your organization, connect with the experts at Trend Micro today.
The post Information security: How Hackers Leverage Stolen Data for Profit appeared first on .
from Trend Micro Simply Security https://ift.tt/2ERs3PZ
Birthday blues for bitcoin as investors face year-on-year loss
from Reuters: Technology News https://ift.tt/2RtTQrd
Apple's New MacBook Disconnects Microphone "Physically" When Lid is Closed
from The Hacker News https://ift.tt/2OZERs5
Sprint beats revenue and profit forecasts, shares rise
from Reuters: Technology News https://ift.tt/2Qa7qPZ
Sprint net subscriber additions blow past estimates
from Reuters: Technology News https://ift.tt/2AC803V
Sprint net subscriber additions blows past estimates
from Reuters: Technology News https://ift.tt/2SyL2Sg
Hackers Use LinkedIn Messages to Spread RAT Malware Through DLL Sideloading
Cybersecurity researchers have uncovered a new phishing campaign that exploits social media private messages to propagate malicious payloads...

-
Original release date: November 08, 2018 Summary JBoss Verify and EXploitation tool (JexBoss) is an open-source tool used by cybersecurity...
-
Original release date: May 21, 2018 The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recorded b...
-
Original release date: January 29, 2018 The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been record...
-
It's no secret that learning how to code is one of the most important things you can do when it comes to the beginning or furthering pra...
-
Original release date: February 12, 2018 The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recor...
-
Original release date: February 26, 2018 The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recor...
-
Os estragos causados pelo ataque com ransomware ao Superior Tribunal de Justiça (STJ) ainda não são totalmente conhecidos. A Polícia Federa...
-
Original release date: January 08, 2018 The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been record...
-
Original release date: March 9, 2020 The CISA Weekly Vulnerability Summary Bulletin is created using information from the NIST NVD . In som...
-
A four-year-old severe vulnerability has been discovered in the Secure Shell (SSH) implementation library known as Libssh that could allow a...